|
|
 |
| Авторизация |
|
|
 |
| Поиск по указателям |
|
 |
|
 |
|
|
 |
 |
|
 |
|
| Bauer F.L. — Decrypted Secrets: Methods and Maxims of Cryptology |
|
|
 |
| Предметный указатель |
Decimation 90 128 238
Decryption key 167 193 195 210
Decryption of ancient scripts 26 37 47 69 Plate
Decryption step 42 43 47 49 194 203
Defense Calculator (IBM 701) 458
Defense Intelligence Agency (DIA) 31
Deflnal 33
Delastelle, Felix Marie 67 179 341 500
DeliaPorta, Giambattista 1 1 39 44 47 58 130 131 140 141 114 211 214 216—217 222 260 268 280 339 340 382
Delta process (Tutte) 403 404
Denary 40 54
Denary cipher 40
Denning, Dorothy E.R. 230 499
Denning, Norman 473
Denniston, Alastair G. 442 477
Denniston, Robin 375 477
Depth 345 350 350—351 357—358 369 375
Depth cribbing 419
Dershavin, Gavrila Romanovich 258
DES 36 184—190 191 193 194 197 226 229 230 236
DES, modes of operation for 188 236
DESAB3 (codebook) 172
Desch BOMBE 454
Desch, Joseph 454—457
Deubner, Ludwig 49 472
Deubner, Ottfried 278
Deutsches Museum Munich VIII
Dia 30
Diacritic marks 39
Diagonal board 173 451—456 482
Diagonally continued alphabets 109
Diccionario Cryptographico (code) 75
Dickinson, Velvalee 17
Dickson,L.E. 83
Dieder group 382
Difference method, difference table 369 370—372 413—415 422
Differential cryptanalysis 189 212
Differenzenrechengeraet 372
Diffusion 174
Digital Signature Algorithm (DSA) 209
Digital Signature Standard (DSS) 209
Digraphic substitution 58—63 64 66 67 78 239 241 248
Dilworth,R.R 496
Dime, Whitfield 6 167 195 209 227
Direction-finding VII 221
Directory 195—197
Discrete logarithm function 168 200—202
Discriminant 173 412 482
Disinformation 4
Disk 39 41 44—45 49 51—52 109 127 139
Division algorithm 91
DNA 486
Dodgson, Charles Lutwidge [Lewis Carroll] 6 130 179 423
Doenitz,Karl 212 221 420 472
Dolphin see 'Hydra' (key net)
Donelly, Ignatius 30
Doppelkassettenverfahren 66
Doppelwuerfelverfahrvn 100
Doppler 335 347 see
Dora (reflector "D") 120 123
Double casket, double PLAYFAIR 66
Double cipher 141 364
Double cribbing 419
Double cross 15 18
Double encipherment of text setting 431—433 see
Double superencryption 421
Double transposition 27 100 216 244 467
Double-ended scrambler 445 446 448 449 451 454
Doublet (letters) 215 216 224 254 439
Doubling (words) 216 254 431 390 392 406 410 440 480
Doubly safe primes 207 210
Douglas, Chevalier 16
Doyle, Arthur Conan 12
Dragon 338 409
Dreher 306
Dreyfus, Alfred 213
Driscoll, Agnes nee Meyer 154 338 454
Du Carlet, Jean Robert 1
Dual encryption steps 379
Ducros, Oliver 134
Dudeney, Henry Ernest 94
DUENNA 287 457
Dulles, Allen Welsh 41 61 278 415
Dummy 21 215 216
dummy text 33 212
Dunning, Mary Jo 155
Duplication 52 111 134 184 442
Durchgamgsraeder 113
Dyer, Thomas H. 333 372
Eachus, Joseph 456—458
Eastcote 454 455
Eastman 5202 344 410
eavesdropping 26 208 212 280 476 480
EBCDIC (code) 55
Eckardt,Heinrich von 484
ECM Mark I II 123 151 481
Edward Duke of Windsor 28
Efficiency boundary 197—198
Efficient (method) 196 197 199 200 204
Ehler, Herbert VIII
EINSing, EINS catalogue 287—288 444
Elble, R. 212
Electric contact realization 110—111
Electronic Code Book (ECB) 36 188—189 204 229
ElGamal, Tahir 209
Elliptic curve method (ECM) 201
Ellis, James H. 6
Encicode 370
Enciphering step, encoding step 35
Encryption and signature methods 195
Encryption block 35
Encryption error 26 98 144 160 210 225 470
Encryption key, open 193—210
Encryption philosophy 223
Encryption security 32 144 153 156 210 211—232
Encryption step 34—36 41—42 44 58 80 106
Encryption table 35 136 368 383 428 430
Encryption width 34—35 106
Encryption, monoalphabetic 35 36 45 49 98 113 140 180 188 203 204 229 238
Encryption, nonperiodic 36 144—145 158
Encryption, periodic 36 140 145 157 168 330 375
Encryption, polyalphabetic 144 157 241—243 248 268 322
Encryption, progressive 110 144—145 157 274 287
Encryption, quasi-nonperiodic 145 158 161 460
Endomorphic encryption 34 36 41 43 46 50 107 169—170 378 379
Endomorphic linear substitution 81 82
Engineering Research Associates, Inc.(ERA) 458
Engstrom, Howard Theodore 338 458
ENIGMA 4 29 32 112—126 146—149 151 153 169 172 215—216 218 220 269 281 338 419 420 431—457 478—484
ENIGMA '11-15-17' see ENIGMA G
ENIGMA A,B 112 114 117 122 146
ENIGMA C 113—117 147 166 281—282
ENIGMA D 117 124—125 147—148 153
ENIGMA equation 118
ENIGMA G 117 118 123 124 125 126 146 148—149 373
ENIGMA G-312 118 125 148—149 373
ENIGMA Grundstellung see basic wheel setting
ENIGMA I 48 118 121 118 166
ENIGMA II 118
ENIGMA replicas 437—441 442
ENIGMA ring setting 121 122 168 219 284 432 437 439—441 448 449 481—482
ENIGMA Ringstellung see ring setting
ENIGMA Spruchschliissel see text setting
ENIGMA superencryption 173 339
ENIGMA T ('Tirpitz') 124 125 148
ENIGMA Tagesschliissel see ground setting
ENIGMA text setting see message setting
ENIGMA, 3-rotor- 118—120 149 156 166 219 220
ENIGMA, 4-rotor- (Kriegsmarine, M4) 4 45 121 156 214—215 219 220 420 431 Plate
ENIGMA, Abwehr- see ENIGMA G
| ENIGMA, basic wheel setting (ground setting) 117 121 122 168 432 433 437—439 441 448
ENIGMA, commercial 92 114 117 281 284 431
ENIGMA, counter- 148
ENIGMA, message setting 122 173 229 416—418 132 435 439 443—444 448—449
ENIGMA, number of ENIGMAs 123
ENIGMA, numbering of 118 120 124 125
ENIGMA, Reichsbahn- 124 125
ENIGMA, rotor order 120 122 432 437—449 454 481—482
ENIGMA, rotors 113—118 120 145—146 Plate
ENIGMA, Wehrmacht- 48 118—120 124 125 126 148—149 168 2—1 284 2—7 288 431
ENIGMAK (INDIGO) 117 126 281
entropy 329 487 494
Enzensberger, Hans Magnus 5
Equifrequency cipher 291
Equivocation 487 489
ERA 1101, ERA 1101 A, ERA 1103 458
Erdoes, Pal 138 496
Eriksson, Bertil E.G. 56
Error-detecting and-correcting codes 26
Erskine, Ralph VII VIII 4 124 416 439 457 482 483 498
Escrowed Encryption Standard (EES) 8 229
Euler's 36-officer problem 59
Euler's totient function 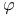 90 203 238 90 203 238
Euler, Leonhard 11 8
European Union 229
Euwe,Max 158
Event, elementary 487
Ewing, Sir Alfred 420
Example 'Boell' 98 245 246 293 294 297 301 304 466
Example 'Kulp' 331 332 345—348 349 351—354 355 369
Exclusion of encryption methods 290—291
Exclusive OR 143
Exhaustion of probable word position, binary non-coincidence 271—272 277
Exhaustion of probable word position, non-coincidence 268—270 277
Exhaustion of probable word position, zig-zag 280—281
Exhaustive search 222 236 237—251
Exponentiation in 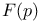 199 200 199 200
EYRAUD encryption step 128
Eyraud, Charles 39 47 63 90 98 99 107 128 131 136 139 295 296 306 307 322 467 500
Eyssen, Capt. 219
Eytan [Ettinghausen], Walter 173
Fabian, Rudolph J. 372
Fabyan, George 30
Factorization 198 199 202 205
Falsification 26
Familes of alphabets 106—138
Family code 19
Family of message blocks 279
Fano, Robert M., Fano condition 36
Feedback cycle system 448—453
Feinstein-Grotjan, Genevieve 155 164
Feistel,Horst 184 185
Fellers, Frank Bonner 475
Fellgiebel, Erich 32 118 212 483
Female 48 224 434 441 446
Fenner.Wilhelm 470
Fermat prime 183 200
Fermat's factorization 205
Fermat's theorem 182
Ferner, Robert 155
Ferris, John 483
Fersen, Axel Graf von 144
Fetterlein, Ernst C.('Felix') 3 172
FIALKA (фиалка) 150
Fiber 33
Fibonacci numbers 176
FIDNET 231
Figl, Andreas 60 61 213 259 296 471 472 480 500
Filby, P.William 172
Finite, finitely generated 34
First Amendment 7
First character 80
Fist 218
Five-digit code 75 76 77
Five-letter code 40 75
fixpoint 177 178 183 206 440 441 450
FLB's resurrection 175
Fleissner grille 96 97
Fleissner von Wostrowitz, Eduard 96 295 500
Fliegerfuehrer Trondheim 447
FLORADORA see GEC
Flowers, T.H. 407
Floyd, Robert W. 157
FLUSZ 61 62
Foersvarsvasendets Radioanstalt (FRA) 32 399
Foppl, Ludwig 128 472
foreign see 'Aegir' (key net)
Formal cipher 38 310
Forschungsamt des RLM 280 472 474
Forschungsstelle der Reichspost 10
Forster, Otto 200
Foss, Hugh 115 116 154 445 478
Four-digit code 75
Fourbesque 15
Fox, Philip E. 286
FRA (Forsvarsvasendets Radioanstalt) 32 399
Fractionating method 66
Franksen, Ole Immanuel 129 341
Franz, Wolfgang 3 269
FREAK 464
Freemasons' cipher 45
Freestyle methods 317 363 494
Frequency count 293 296 298 299 302
Frequency distribution 59 290—291 295—296 299
Frequency profile 292—294 352—353 360
Frequency, ordering 294—297 299 300
Freyss, Gustave 469
Friderici, Joannes Balthasar 40
Friedman examination 331 341 343 344 348 349 486
Friedman, Elizebeth Smith 5 256
Friedman, William Frederick 2 30 31 68 75 78 79 86 123 133 134 136 140 150—152 155 163 230 234 235 247 256 272 277 280 281 317 320 331 333 336 339 341 343 344 348 349 373 374 377 401 416 424 428 471 483 486 497
Friedmann (code) 75
Friedrich, J. 26
Friedrichs, Asta 69 278 415
Frowein, Hans-Joachim 472
Fuchs, Klaus 164
Function inversion 196—197
Functional 33
Funkschluessel C. 117 118
Funkschluessel M 118 121
Funkspiel 209 218
G.2 A.6 31 69 216
G.C.&C.S. 3 31 63 92 442 443 470
GADFLY (key net) 448
Gagliardi, Francesco 103
Galilei, Galileo 103
Galland (code) 75
Galois field 81 181
Games, Helen Fouche 60 63 97 98 179 252 255 257 264 290 295 296 306 310 312 497
Garbling and corruption of messages 26
gardening 420 480
Gardner, Martin 354
Garlinski, Jozef 437 498
Gau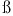 , Carl Friedrich 202 , Carl Friedrich 202
Gaujac,Paul 213
Gaussin, Joseph 129
Gay hurst 454
GEC 172 421 484
GEE (one-time-pad system) 164 165
Geheimklappe 63 69 78
Geheimschreiber 170—171 387—389 395 396 398 400 483
Geiger counter 164
Gematria 37
Generating relation of encryption steps 34
Generation of a quasi-nonperiodic key 157
Generatrix 134 273—277 279
Genuine reflection 48 51 60 116
George, Stefan 5
Gerold, Anton VIII 210
Gewerhschaft Securitas 111
|
|
 |
| Реклама |
 |
|
|
 |
|
О проекте
|
|
О проекте



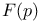
 , Carl Friedrich
, Carl Friedrich