|
|
 |
| Авторизация |
|
|
 |
| Поиск по указателям |
|
 |
|
 |
|
|
 |
 |
|
 |
|
| Stinson D.R. — Cryptography: Theory and practice |
|
|
 |
| Предметный указатель |
Abelian group 4
Access structure 486
Access structure, basis 487
Access structure, connected 503
Access structure, ideal decomposition 510
Access structure, minimal authorized subset 487
Access structure, monotone property 487
Access structure, threshold 487
Active adversary 362
Active S-box 84
Adaptive algorithm 250
Additive identity 3
Additive inverse 4
Adjoint matrix 17
Advanced Encryption Standard 102
Adversary, active 362
Adversary, passive 363
AES 102
Affine Cipher 11
Affine function 8
Affine — Hill Cipher 42
Algorithm, (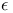 , ,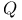 ) 123 ) 123
Algorithm, adaptive 250
Algorithm, deterministic 178
Algorithm, generic 246
Algorithm, Las Vegas 123
Algorithm, non-adaptive 249
Algorithm, randomized 123
ALICE 1
Almost strongly universal hash family 155
Associative property 3
Associative property, of cryptosystems 69
Associative property, of elliptic curve 257
Attack model 26
Attack model, for cryptosystem 26
Attack model, for identification scheme 362
Attack model, for signature scheme 284
Attack, chosen ciphertext 26
Attack, chosen message 284
Attack, chosen plaintext 26
Attack, ciphertext only 26
Attack, dictionary 448
Attack, key-only 284
Attack, known LL-key 396
Attack, known message 284
Attack, known plaintext 26
Attack, known session key 396
Attack, off-line 449
Attack, parallel session 357
Authenticated encryption 145
Authenticated key agreement scheme 396
Authentication matrix 146
Authentication tag 120
Authentication, entity 353
authentication, mutual 363
Authorized subset 486
Autokey cipher 24
Average-case success probability 123
Basis 487
Bayes’ Theorem 48
Bellare — Rogaway SKDS 421
BES 518
Bias 80
Big MAC attack 142
Binomial coefficient 33
Birthday paradox 125
Bit generator 323
Bit generator, pseudo-random 323
Bit generator, seed 323
Bit predictor 330
Bit predictor, next 330
Bit predictor, previous 339
Bivariate Lagrange interpolation formula 404
BKDP 525
Blacklisting Scheme 533
Block 410
Block cipher 21
Block length 74
Blom Key Predistribution Scheme, 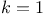 400 400
Blom Key Predistribution Scheme, arbitrary 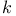 403 403
Blum — Blum — Shub generator 336
Blum — Goldwasser Public-key Cryptosystem 346
Bob 1
Boolean circuit 488
Boolean circuit, fan-in 488
Boolean circuit, fan-out 488
Boolean circuit, monotone 488
Boolean formula 488
Boolean formula, conjunctive normal form 491
Boolean formula, disjunctive normal form 488
Brickell Secret Sharing Scheme 499
Broadcast encryption scheme 518
Broadcast encryption scheme, privileged subset 518
Broadcast key distribution pattern 525
Burmester triangle attack 443
Burmester — Desmedt Conference KAS 451
Caesar cipher 4
Candidate subkey 87
CBC mode 109
CBC — MAC 144
CCM mode 112
CDH 273
Certificate 367
Certificate path 464
Certificate path validation 465
Certificate path, trust model 464
Certificate path, validation 465
Certificate Revocation 458
Certificate Revocation List 464
Certificate validation 463
Certificate, issuance 458
certificate, revocation 458
Certificate, validation 463
Certificate, X. 509 461
Certification Authority 458
Certification authority, hub 466
CFB mode 111
Challenge 356
Challenge-and-response, for identificaiton scheme 356
Challenge-and-response, for signature scheme 307
Channel 1
Chaum-van Antwerpen Signature Scheme 308
Chinese remainder theorem 170
Chosen ciphertext attack 26
Chosen message attack 284
Chosen plaintext attack 26
cipher block chaining mode 109
cipher feedback mode 109
Ciphertext 1
Ciphertext only attack 26
Ciphertext, stream cipher 22
CKAS 450
Client 459
Closed 3
Cocks Identity-based Public — Key Cryptosystem 475
Code 542
Code, descendant 542
Code, identifiable parent property 543
Code, IPP 543
Code, Reed — Solomon code 551
Code, TA 549
Codeword 542
Codeword, parent 542
Collision Resistant 121
Commutative cryptosystems 69
Commutative property 3
Complete graph 503
Complete multipartite graph 503
Completeness 372
Composite Quadratic Residues problem 338
| composition 141
Compression function 120
Computational Diffie — Heilman problem 273
Computational security 45
Concave function 59
Concave function, strictly 59
Conditional entropy 62
Conditional probability 47
Conference key agreement scheme 450
Congruence 3
Congruence, of polynomials 251
Congruent 3
Conjunctive normal form 491
Connected access structure 503
Continued fraction 208
Convergent continued fraction 208
Counter 111
counter mode 111
Counter with cipher-block chaining mode 109
Cover-free family 410
CREDENTIAL 353
CRL 464
cross-certification 466
Cryptanalysis 6
Cryptosystem 1
Cryptosystem, distinguishability of ciphertexts 215
Cryptosystem, endomorphic 67
Cryptosystem, idempotent 69
Cryptosystem, partial break 215
Cryptosystem, product 67
Cryptosystem, public-key 161
Cryptosystem, symmetric-key 161
Cryptosystem, total break 215
Cyclic group 171
Data Encryption Standard 95
DDH 273
Dealer 481
Deception probability 146
Decision Diffie — Hellman problem 273
Decision problem 178
Decomposition construction 510
decryption 473
Decryption rule 1
Decryption rule, stream cipher 22
Degree of polynomial 251
Degree of recurrence 23
Delta CRL 464
Denning — Sacco attack 416
DES 95
Descendant code 542
Determinant 16
Deterministic algorithm 178
dictionary attack 448
Differential 91
Differential cryptanalysis 89
Differential trail 92
Diffie — Hellman Key Agreement Scheme 430
Diffie — Hellman Key Predistribution Scheme 397
Diffie — Hellman problem, computational 273
Diffie — Hellman problem, decision 273
Digital Signature Algorithm 295
Digram 27
Disavowal protocol 307
Discrete logarithm 234
Discrete Logarithm Generator 351
Discrete logarithm problem 234
Discrete Logarithm problem, bit security 268
Discrete Logarithm problem, generic algorithm 246
Discrete Logarithm problem, Index calculus algorithm 244
Discrete Logarithm problem, Pohlig — Hellman algorithm 243
Discrete Logarithm problem, Pollard rho algorithm 240
Discrete Logarithm problem, Shanks’ algorithm 237
Discrete random variable 46
Disjunctive normal form 488
Disruption 364
Distinguishabilityof ciphertexts 215
Distinguishable probability distributions 329
Distinguisher 329
Distinguisher, polynomial-time 329
Distribution rule 493
Distributive property 4
Division of polynomials 251
DSA 295
Dynamic group 517
ECB mode 109
ECDSA 298
ECIES 264
EKE 450
Electronic codebook mode 109
Elgamal Public-key Cryptosystem 235
Elgamal Signature Scheme 288
Elliptic Curve Digital Signature Al¬gorithm 298
Elliptic Curve Factoring algorithm 189
Elliptic Curve Integrated Encryption Scheme 264
Elliptic curve, group 255
Elliptic curve, modulo 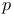 258 258
Elliptic curve, non-singular 255
Elliptic curve, over the reals 255
Elliptic curve, point at infinity 255
Elliptic curve, point compression 262
Elliptic curve, singular 255
Encoding 248
Encrypted Key Exchange 450
Encryption 473
Encryption matrix 49
Encryption rule 1
Encryption rule, stream cipher 22
End user 464
Endomorphic cryptosystem 67
Entity authentication 353
entropy 55
Entropy, conditional 62
Entropy, of a natural language 64
Euclidean algorithm 164
Euclidean algorithm, extended 166
Euler phi-function 9
Euler pseudo-prime 182
Euler’s criterion 180
Event 47
Exclusive-OR 22
Exhaustive key search 6
Existential forgery of a MAC 158
Existential forgery of a signature scheme 285
Expansion function 96
Expansion, continued fraction 208
Explicit key confirmation 435
Extended Euclidean algorithm 166
Factor base 194
Factor base, for discrete logarithms 244
Factoring, elliptic curve algorithm 189
Factoring, general number field sieve 201
Factoring, number field sieve 199
Factoring, Pollard  algorithm 190 algorithm 190
Factoring, Pollard rho algorithm 193
Factoring, quadratic sieve 199
Factoring, random squares algorithm 196
Factoring, trial division 189
Fail-stop signature scheme 313
Fan-in 488
Fan-out 488
Federal Information Processing Standards 95
Feige — Fiat — Shamir Identification Scheme 388
Feistel cipher 95
Fermat’s theorem 171
Fiat — Naor KDP 409
Fiat — Shamir signature scheme 317
Field 10
Field of prime power order 250
Filtering operation 94
Fingerprint 540
|
|
 |
| Реклама |
 |
|
|
 |
|
О проекте
|
|
О проекте



 ,
, )
) 
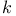
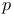
 algorithm
algorithm