|
|
 |
| Авторизация |
|
|
 |
| Поиск по указателям |
|
 |
|
 |
|
|
 |
 |
|
 |
|
| Stinson D.R. — Cryptography: Theory and practice |
|
|
 |
| Предметный указатель |
Fingerprint, hybrid 541
fips 95
Flow 357
Forger 141
Forger, (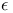 , , 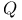 ) 141 ) 141
Forgery 141
Forgery, existential 158
Forgery, of a MAC 141
Forgery, of a signature 282
Forgery, selective 158
Full Domain Hash 304
Function, injective 2
Function, surective 19
General number field sieve 201
generic algorithm 246
Generic algorithm, adaptive 250
Generic algorithm, non-adaptive 249
Girault Key Agreement Scheme 446
Goldwasser — Micali Public-key Cryptosystem 345
Graph, complete 503
Graph, complete multipartite 503
Group 4
Group isomorphism 247
Group key 407
Group, abelian 4
Group, cyclic 171
Group, elliptic curve 255
Group, order of element 170
Guillou — Quisquater Identity-based Identification Scheme 387
Guillou — quisquateridentification Scheme 384
Hamming distance 549
Hash family 120
Hash family, (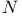 , ,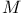 ) 120 ) 120
Hash family, almost strongly universal 155
Hash family, keyed 120
Hash family, perfect 544
Hash family, separating 545
Hash family, strongly 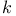 -universal 159 -universal 159
Hash family, strongly universal 149
Hash function 120
Hash function, collision resistant 121
Hash function, ideal 122
Hash function, iterated 129
Hash function, one-way 121
Hash function, preimage resistant 121
Hash function, second preimage resistant 121
Hill cipher 18
HMAC 143
Honest participant 362
Honest verifier 377
Hub CA 466
Hub-and-spoke configuration 466
Huffman’s algorithm 58
Hybrid fingerprint 541
Ideal decomposition 510
Ideal secret sharing scheme 498
Idempotent cryptosystem 69
Identifiable parent 543
Identifiable parent property 543
Identification 353
Identification, (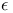 , , 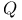 )-secure 360 )-secure 360
Identification, (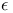 , , 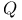 , , 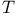 )-secure 360 )-secure 360
Identification, active adversary 362
Identification, honest participant 362
Identification, honest verifier 377
Identification, identification scheme 353
Identification, identity-based 386
Identification, information-gathering phase 363
Identification, intended peer 362
Identification, matching conversations 362
Identification, mutual 363
Identification, passive adversary 363
Identification, sound 376
Identification, zero-knowledge 377
Identity matrix 14
Identity-based identification scheme 386
Identity-based public-key cryptosystem 473
Identity-based public-key cryptosystem, master key 473
Identity-based public-key cryptosystem, master private key 473
Identity-based public-key cryptosystem, master public key 473
Identity-based public-key cryptosystem, system parameters 473
Identity-based public-key cryptosystem, user private key 473
Identity-based public-key cryptosystem, user public key 473
Impersonation 146
Implicit key authentication 435
Implicit key confirmation 435
Incidence matrix 410
Independent random variables 47
Index calculus algorithm 244
Index of coincidence 33
Induced subgraph 508
information 54
Information rate 497
Information theory 54
Information-gathering phase 363
Initial permutation 96
Initialization vector 109
Injective function 2
Input x-or 89
Intended peer 362
Interactive protocol 356
Interactive protocol, flow 357
Interactive protocol, session 357
Intruder-in-the-middle 361
Inverse matrix 15
Inverse, additive 4
Inverse, elliptic curve 257
Inverse, matrix 15
Inverse, multiplicative 10
Inverse, permutation 19
Inverse, polynomial 252
Involutory key 39
IPP code 543
Irreducible 252
Isomorphism 247
Iterated cipher 73
Iterated hash function 129
Iterated hash function, output transformation 130
Iterated hash function, preprocessing step 130
Iterated hash function, processing step 130
Jacobi symbol 181
Jensen’s Inequality 59
Joint probability 47
KAS 394
Kasiski test 32
KDP 406
Kerberos 418
Kerckhoffs’ principle 26
Key 1
Key agreement scheme 394
Key agreement scheme, authenticated 396
Key agreement scheme, conference 450
Key agreement scheme, password-based 448
Key agreement scheme, two-flow 438
Key authentication, implicit 435
Key confirmation 416
Key confirmation, explicit 435
Key confirmation, implicit 435
Key confirmation, mutual 420
Key derivation function 442
Key distribution pattern 406
Key distribution pattern, broadcast 525
Key equivocation 62
Key establishment 393
Key legitimacy field 469
Key predistribution scheme 393
Key revocation algorithm 517
Key schedule 73
Key transport scheme 426
Key, for hash family 120
| Key, for signature scheme 282
Key, group 407
Key, long-lived 394
Key, semantic security 399
Key, session 394
Key, stream cipher 22
Key-only attack 284
keyring 469
Keyspace 1
Keyspace, for hash family 120
Keyspace, for signature scheme 282
Keystream 22
Keystream alphabet 22
Keystream generator 22
Keyword 12
KLF 469
Knowledge 354
Known LL-key attack 396
Known message attack 284
Known plaintext attack 26
Known session key attack 396
KPS 393
Lagrange interpolation formula 404
Lagrange’s Theorem 170
Lamport Signature Scheme 300
Las Vegas algorithm 123
Latin square 70
Latin Square Cryptosystem 70
Legendre symbol 181
Lifetime 418
Linear approximation table 84
Linear congruential generator 324
Linear cryptanalysis 84
Linear feedback shift register 24
Linear recurrence 23
Linear transformation 14
Little MAC attack 142
LL-key 394
Logical Key Hierarchy 537
Long-lived key 394
Lucifer 95
MAC 119
MAC, (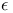 , , 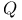 )-secure 360 )-secure 360
MAC, (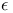 , , 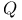 , , 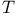 )-secure 360 )-secure 360
MAC, nested 141
Marking assumption 541
MARS 102
Matching conversations 362
Matrix product 14
Matrix, identity 14
Matrix, inverse 15
Matrix, rank 315
MD4 139
MD5 139
Memoryless source 56
Merkle — Damgard construction 131
Mesh configuration 466
message authentication code 119
Message digest 120
Message, for hash function 120
Message, for signature scheme 282
Message, signed 282
Miller — Rabin algorithm 188
Minimal authorized subset 487
Mitchell — Piper KDP 410
Mode of operation 109
Modular arithmetic 3
Modular exponentiation 176
Modulus 3
Monoalphabetic cryptosystem 12
Monotone boolean circuit 488
Monotone circuit construction 489
Monotone property 487
Monte Carlo 178
Monte Carlo algorithm 178
Monte Carlo algorithm, error probability 178
Monte Carlo algorithm, no-biased 178
Monte Carlo algorithm, yes-biased 178
MTI problem 456
MTI/Azero Key Agreement Scheme 439
MTI/Azero Key Agreement Scheme, Burmester triangle attack 443
MTI/Azero Key Agreement Scheme, known session key attack 442
Multicast 517
Multicast re-keying scheme 531
Multiplicative identity 4
Multiplicative inverse 10
Mutual authentication 363
Mutual identification 363
Mutual key confirmation 420
NAF representation 265
Naor — Pinkas Rekeying Scheme 535
National Institute of Standards and Technology 95
Nearest neighbor 549
Nearest neighbor decoding 549
Needham — Schroeder SKDS 415
Needham — Schroeder SKDS, Denning — Sacco attack 416
Nested MAC 141
Next bit predictor 330
NIST 95
Non-adaptive algorithm 249
Non-adjacent form 265
Non-singular elliptic curve 255
Non-synchronous stream cipher 24
NP-complete 45
Number field sieve 199
OAEP 224
OCSP 464
OFB mode 111
Off-line attack 449
Okamoto Identification Scheme 379
one-time pad 53
One-way function 121
One-way function, trapdoor 163
Online certificate status protocol 464
Optimal Asymmetric Encryption Padding 224
Oracle 122
OSCAR 1
OTF 469
output feedback mode 109
Output transformation 130
Output x-or 89
Owner trust field 469
Padding function 130
Pairing 479
Parallel session attack 357
Parent 542
Partial break 215
Partial break, of cryptosystem 215
Passive adversary 363
Password 448
Password-based key agreement scheme 448
Path discovery 467
perfect forward secrecy 396
Perfect hash family 544
Perfect secrecy 50
Perfect secret sharing scheme 487
Periodic stream cipher 22
Permutation 19
Permutation Cipher 19
Permutation matrix 21
Permutation, inverse 19
Personal Identification Number 354
PGP 468
PGP, key legitimacy field 469
PGP, keyring 469
PGP, owner trust field 469
PHF 544
Piling-up lemma 81
PIN 354
Pirate decoder 548
|
|
 |
| Реклама |
 |
|
|
 |
|
О проекте
|
|
О проекте



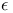 ,
, 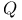 )
) 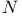 ,
,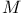 )
) 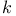 -universal
-universal 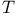 )-secure
)-secure