|
|
 |
| Авторизация |
|
|
 |
| Поиск по указателям |
|
 |
|
 |
|
|
 |
 |
|
 |
|
| Stinson D.R. — Cryptography: Theory and practice |
|
|
 |
| Предметный указатель |
PKI 457
PKI networking 466
Plaintext 1
Plaintext, stream cipher 22
Pohlig — Hellman algorithm 243
Point 410
Point at infinity 255
Point compression 262
Pollard  algorithm 189 190 algorithm 189 190
Pollard rho algorithm for discrete logarithms 240
Pollard rho algorithm for factoring 193
Polyalphabetic cryptosystem 13
Polynomial congruence 251
Polynomial interpolation 404
Polynomially equivalent 175
Prefix-free encoding 57
Preimage Resistant 121
Preprocessing step 130
Pretty Good Privacy 468
Previous bit predictor 339
Prime 9
Prime number theorem 178
Primitive element 171
Primitive element, modulo 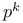 276 276
Principal square root 338
Private key 161
Privileged subset 518
Probabilistic method 410
Probabilistic public-key cryptosystem 345
Probabilistic public-key cryptosystem, randomizer 345
Probabilistic public-key cryptosystem, security parameter 345
Probabilistic Signature Scheme 318
probability distribution 46
Probability distributions, distinguishable 329
Probability, conditional 47
Probability, joint 47
Processing step 130
Product cryptosystem 67
Proof of knowledge 376
Propagation ratio 91
Protocol failure 228
Provable security 45
Pseudo-random bit generator 323
PSS 318
Public key 161
Public key, self-certifying 444
Public-key cryptosystem 161
Public-key cryptosystem, identity-based 473
Public-key cryptosystem, probabilistic 345
Public-key infrastructure 457
Public-key infrastructure, certificate issuance 458
Public-key infrastructure, certificate revocation 458
Public-key infrastructure, certification authority 458
Public-key infrastructure, key backup 458
Public-key infrastructure, key recovery 458
Public-key infrastructure, key update 458
Public-key infrastructure, timestamping certificates 458
Quadratic non-residue 179
Quadratic reciprocity 183
Quadratic residue 179
Quadratic sieve 199
Quotient of polynomials 251
Rabin cryptosystem 211
Ramp scheme 528
Random oracle model 122
Random squares algorithm 196
Random variable, discrete 46
Random variable, entropy 55
Random variable, independent 47
Randomized algorithm 123
Rank 315
RC 6 102
Recurrence 23
Recurrence, degree 23
Recurrence, linear 23
Redundancy of a natural language 64
Reed — Solomon code 551
Relatively prime 9
Remainder of polynomials 251
Right pairs 94
Rijndael 102
Ring 4
Ring, of polynomials 251
round 73
ROUND function 73
Round key 73
Round key mixing 75
RSA cryptosystem 173
RSA generator 326
RSA Signature Scheme 283
S-box 74
S-box, balanced 116
S-box, linear approximation 84
Schnorr Identification Scheme 372
Schnorr Signature Scheme 294
Second preimage resistant 121
Secret sharing scheme 487
Secret sharing scheme, access structure 486
Secret sharing scheme, authorized subset 486
Secret sharing scheme, distribution rule 493
Secret sharing scheme, ideal 498
Secret sharing scheme, information rate 497
Secret sharing scheme, perfect 487
Secure Socket Layer 460
Security 45
Security, computational 45
Security, provable 45
Security, semantic 215
Security, unconditional 46
Seed 323
Selective forgery of a MAC 158
Selective forgery of a signature scheme 285
Self-certifying public key 444
Semantic security 215
Separating hash family 545
Serpent 102
server 459
session 357
Session key 394
| Session key distribution scheme 393
Session key distribution scheme, secure 422
Session key, lifetime 418
Session, transcript 377
Set system 410
Set system, block 410
Set system, cover-free family 410
Set system, incidence matrix 410
Set system, point 410
SHA 139
SHA-224 139
SHA-256 139
SHA-384 139
SHA-512 139
SHA-one-pad 138
Shamir Ramp Scheme 529
Shamir Threshold Scheme 482
Shanks’ algorithm 237
SHARE 481
SHF 545
Shift cipher 4
Shrinking generator 326
Signature 282
Signature scheme 282
Signature scheme, existential forgery 285
Signature scheme, fail-stop 313
Signature scheme, non-deterministic 287
Signature scheme, one-time 299
Signature scheme, selective forgery 285
Signature scheme, total break 284
Signature scheme, undeniable 307
Signed binary representation 265
Signed binary representation, non-adjacent form 265
Signed message 282
Signing algorithm 282
Single source broadcast 517
Singular elliptic curve 255
SKDS 393
Smooth integer 197
Solovay — Strassen algorithm 182
Soundness 376
SPN 74
Spurious keys 64
Spurious keys, expected number of 66
Square 113
Square root, principal 338
Square-and-multiply algorithm 177
SSL 460
State 73
Station-to-station Key Agreement Scheme 433
Steiner — Tsudik — Waidner Conference KAS 453
Stirling’s formula 72
Stream cipher, non-synchronous 24
Stream cipher, periodic 22
Stream cipher, synchronous 22
Strict hierarchy 464
Strictly concave function 59
String 2
Strongly 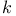 -universal 159 -universal 159
Strongly universal 149
Subkey 73
Substitution 146
Substitution Cipher 7
Substitution-permutation network 7 4
Success probability, average-case 123
Success probability, worst-case 123
Surjective functipn 19
Suspect coalition 542
Symmetric-key cryptosystem 161
Synchronous stream cipher 22
TA code 549
Threshold access structure 487
Threshold scheme 481
Threshold scheme, dealer 481
Threshold scheme, key 481
Threshold scheme, share 481
timestamp 420
Timestamping certificates 458
Total break 215
Total break, of cryptosystem 215
Total break, of signature scheme 284
Transcript 377
Transposition Cipher 19
Trapdoor 162
Trapdoor one-way function 163
Trapdoor one-way permutation 219
Trial division 189
Trigram 27
Trust anchor 464
Trust model 464
Trust model, strict hierarchy 464
Trust model, web browser 467
Turing reduction 213
Twofish 102
UMAC 155
Uncertainty 54
Unconditional security 46
Undeniable signature scheme 307
Unicity distance 66
Universal test 333
Unknown key-share attack 455
Unknown-key collision attack 142
Valid pair 120
Van Heyst and Pedersen Signature Scheme 313
Vector space construction 498
Verification algorithm 282
Vigenere cipher 12
Virtual conference 517
Web browser model 467
Whitening 75
Wide trail strategy 108
Wiener’s algorithm 210
Word 107
Worst-case success probability 123
X-or propagation ratio 91
X.500 name 461
X.509 certificate 461
XOR — MAC 154
Zero-knowledge identification scheme 377
|
|
 |
| Реклама |
 |
|
|
 |
|
О проекте
|
|
О проекте



 algorithm
algorithm 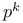
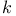 -universal
-universal