|
|
 |
| јвторизаци€ |
|
|
 |
| ѕоиск по указател€м |
|
 |
|
 |
|
|
 |
 |
|
 |
|
| Ullman J.D. Ч Principles of database systems |
|
|
 |
| ѕредметный указатель |
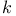 -of- -of-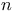 strategy 436 438 440 strategy 436 438 440
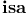 13Ч14 13Ч14
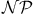 -completeness 93 241 264 267 315 348 387 -completeness 93 241 264 267 315 348 387
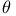 -join 155 -join 155
Absolute address 37
Acyclic Bachman diagram 347
Acyclic hypergraph 335Ч338 419
Acyclic polygraph 387Ч388
ADABAS 121
Address calculation search see УInterpolation searchФ
Adiba, M. 449
Aggregate function 175 181 186 195Ч196 203Ч204 360
Aho, A. V 39 93 172 210 241 264 266 293 315 347
Algebraic dependency 266(see also УDependencyФ)
Algebraic manipulation 272Ч283
Allman, E. 172 210
ANSI/SPARC 34
Applications programmer 5
Arity 20 152
ArmstrongТs axioms aee Axioms
Arnold, R. S. 210
Arora, A. 265
ASSIGNMENT 175 177 182 192Ч193 199Ч200
Associative law 276
Astrahan, M. M. 67 149 172 210 315
atom 156Ч157 162
Attribute 13 20
Atzeni, P. 348
Augmentation 218 245
Authorization table 359
Automatic insertion 115Ч116
Average 175
Avni, H 93
awk 210
Axioms 217Ч220 245Ч246 266
B-tree 58Ч65 68 88Ч89 150 285 391Ч392 407
Bachman diagram see УAcyclic Bachman diagramФ
Bachman, C. W. 35
Backup copy 396Ч397
Bancilhon, F. 173
Bayer, R. 93 407
Beck, L, L 368
Beeri 241 247 264Ч267 347
Bentley, J. L. 93
Berman, R. 172 210
Bernstein, P. A. 241 264Ч265 267 347Ч348 387 407Ч408 449
Binary search 48
Binding 177
Biskup, J 265
Blank tuple variable 318
Blasgen, M. W. 172
Block 36Ч37 40
Block access 37
Bolour, A. 81 93
Bound variable 157Ч158
Boyce Ч Codd normal form 234Ч241
Boyce, R. F. 210
Bucket 40 55 80 131
Bucket directory 40
Burkhard, W. A. 93 190
Cadiou, J. Ч M. 210
CALC-key 104 109Ч110 131
candidate key 217
Cardenas, A, F 121 144
Carlson, C R 265 346
Cartesian product 19 152 177Ч178 181Ч182 268Ч269 273Ч277 289 300
Casanova, M. 267
Cascade, of functions 276
Casey, R. 265
Central node method 439Ч440
Ceri, S. 449
Chain mode 106
Chain query 420Ч424
Chaining, of blocks 54
Chamberlin, D. D 172 210 315
Chandra, A, K. 172 266 315
Chang, C. L 210 347
Chang, P. Y. 315
Chase 259Ч262
Chen, P. P. 35
Childs, D. L 172
Chin, F. Y 368
Chiu, D. W. 449
Choice (operator) 424Ч427
Closure, of a set of attributes 220Ч223
Closure, of a set of dependencies 220Ч221 223 232Ч233 248-249
Cluster 424
Clustering index 284Ч287
COBOL 94
CODASYL 34 94 121
Codd, E. F. 151 172Ч174 210 264Ч265
Coffman, E. G. 408
Comer, D. 93
Committed transaction 397Ч398 403- 442Ч443
Common subexpression 273
Commutative law 275
Compacted tree 424
Complementation 152 245
Complete language 174 178Ч179 182 189 193Ч194 207-208
Complete set of inference rules 217 219Ч220 247
composition 162 182 187
Computational complexity see УSpace complexityФ УTime
Conceptual database 6
Conclusion row 254
Concurrency 4 369Ч410 431Ч450
Condition box 205
Conjunctive query 297Ч298
Connection graph 290Ч296
Connection, in hypergraph 336Ч338 346
Consistency constraint 4(see also УDependencyФ)
Constraint 298(see also УDependencyФ)
Constraint table 354Ч355
Containment, of tableaux 302Ч305
COUNT 175
Cover, of a set of dependencies 223Ч224
Covering, of a key value 48
crash recovery 395Ч400 443Ч447
Culik, K. H. 93
Currency pointer 106Ч108 136
Current of record type 107
Current of run unit 107 109 114Ч115
Current of set type 107
Current parent 139Ч140
Cyclic hypergraph 332Ч338 418Ч419
Dag see УDirected acyclic graphФ
dangling pointer 37 39
Dangling tuple 227 311 332
Data Definition Language 2 10 98Ч99 129 344Ч345
Data dependency 211(see also УDependencyФ)
data independence 9
Data item 94(see also УFieldФ)
Data Manipulation Language see УQuery languageФ
Data model 6Ч7 18(see Network Relational
Database 1
Database administrator 5
Database key 104 110
Database management system 1
Database manger 3
Database record 131
Database scheme 21
Database state see УInstance of
DaTaSyS 172
Date, C J 144
Dayal, U 265 449
DBMS see УDatabase management system
DBTG DDL 94Ч102 356
DBTG DML 108Ч120
DBTG set 95Ч100
DDL see УData definition languageФ
De Jonge, W 210
| Deadlock 373Ч374 380 396 443Ч445
Decomposition rule 219 247
Decomposition, of relation schemes 225Ч234 237Ч243 251-252
Defined trigger 352Ч353
Degree see УArityФ
Delayed evaluation 177Ч178
DELETE 119 141Ч142
Deletion 42Ч43 51 55Ч56 61Ч62 65 74Ч75 115Ч116 118Ч120 133Ч134 141Ч142 184Ч185 192 204 415
Deletion anomaly 212
Deletion bit 39 41 133
Delobel 265Ч266
DelPOrco, P 210
Demers, A 266
DeMillo, R, A 367
DeMorganТs laws 207
Denning, D E 367Ч368
Denning, P J 367 408
Dense index 65Ч68 150
Dependency see УConsistency constraintФ УData УExistence УFunctional УGeneralized УJoin УMultivalued УSubset
Dependency basis 247Ч249
dictionary order see УLexicographic orderФ
Difference 152 158 177 181 191Ч192 277
Direct mode 104
Directed acyclic graph 407
Dissection 292Ч296
Distinguished variable 298
Distributed database system 409Ч450
DL/I 136Ч142
DML see УQuery languageФ
Dobkin, D. P. 367
DOM 159
Domain 206
Domain calculus 162Ч168 197
Domain variable 162
Douque, B. C M 35
Duplicate tuples 186Ч187 193 203
Duplication, of attributes 334Ч335
Duplication, of items 410
Ear, of a hypergraph 335
El Masri, R 35 173
Element, of a record format 70
Ellis, C. S. 407
Embedded dependency 255Ч256 260
Embedded multivalued dependency 252Ч253 255 266 345
Entity 12Ч13
entity-relationship diagram 17Ч18
Entity-relationship model 11Ч18 21Ч22 27Ч28 146
Epstein, R. 449
Equality-generating dependency 254 258Ч259 264
equijoin 155 182 300 477
Equivalence, of expressions 275(see also УStrong equivalenceФ УWeak
Equivalence, of schedules 376Ч377 385Ч387
Equivalence, of tableaux 306Ч307
Essential symbol 330
Eswaran, K. P. 407
Exclusive lock see УWrite lockФ
Existence constraint 115(see also УDependencyФ УInclusion
Existential quantifier 157Ч158
Expression 158 163 274Ч275
Extension see УInstance of
Extension, in ISBL 181
External storage 36Ч37
Fagin, R 247 264Ч267 346Ч347 367
Fernandez, E 367
FETCH 426
Field 36
FILE 36
File Manager 3
File server 410
find 109Ч115
Finite relation 20 152 159Ч160
Finkel, R. A. 93
First normal form 235
Fischer, P C 267
Ford, J. 172 210
Forest 30
Formula 157Ч158 162
fourth normal form 250Ч252
Fragment, of a relation 410Ч416
Fredman, M. L. 93
Free variable 157Ч158 183
Friedman, J H 93
Full dependency 255 261
Full/empty bit 41 56
Functional dependency 211 213Ч248 253- 339 350
Furtado, A, L 173
Galil, Z. 266
Gallaire, H 172
Garbage collection 39
Garcia Ч Molina, H 439 449
Garey, M R. 93 241
Generalized dependency 253Ч262
get 108Ч109 136Ч140
Ginsburg, S. 265
Goodman, N. 266Ч267 347Ч348 408 449
Gotlieb 93 315
Gotlieb, L R. 93
Gouda, M G. 449
Graham reduction 3 5
Graham, M H 335 347
Granularity 370 408
Gray, J. N 407Ч408 449
Greenblatt, D 210
Griffiths, P P. 315 367(see P.
guard condition 413Ч414
Gudes, E 93
Gurevich, Y. 266
Hadzilacos, V. 407
Hagihara, K 266
Hall, P A V 315
Hammer, M. 35 210
Haq, M I 367
Harel, D 172
Hash function 40 43 46(see
Hashing 40Ч46 68 104 146Ч147
Heap 39Ч40 145Ч146
Heath, I. J. 264
Held, G 93 146 172 210
Hierarchical model 30Ч32 122Ч144
Ho, Y. Ч C. 449
Hoffman, L. J. 367
Honeyman, P. 265 346Ч348
Hopcroft, J. E. 39 93 241 293
Horizontal fragment 411
Horowitz, E. 93
Host language 11 106
Howard, J. H. 247 264Ч265
Hsiao, D. K. 367
Hull, R 265
Hunt, H 408
Hypergraph 290 332Ч338 418Ч419
Hypothesis row 254
IDMS 121
image size 285 426 429
Implicational dependency 266(see also УDependencyФ)
IMS 67 128 144 350 356
Inclusion dependency 267(see also УDependencyФ УExistence
Inconsistency 125 212(see
Independence, of operators 172
Independent components 265
INDEX 271Ч272 284(see УIsamФ УSecondary УSparse
Indexed sequential access method see УIsamФ)
Inference, of dependencies 216 256 258Ч262 264 266 323(see
Inference, of inequalities 305Ч306
Infinite relation 152 260
Ingres 146Ч147 190 367
Insert 118 140Ч141
insertion 42 50Ч51 55 61 65 74Ч75 115Ч118 133Ч134 140Ч141 184 192 204 415
Insertion anomaly 212
Instance, of a database 8
|
|
 |
| –еклама |
 |
|
|
 |
|
ќ проекте
|
|
ќ проекте



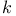 -of-
-of-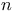 strategy
strategy 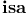
 -completeness
-completeness  -join
-join