Авторизация
Поиск по указателям
Zelkowitz M. — Advances in Computers, Volume 55
Обсудите книгу на научном форуме Нашли опечатку?
Название: Advances in Computers, Volume 55Автор: Zelkowitz M. Аннотация: Volume 55 covers some particularly hot topics. Linda Harasim writes about education and the Web in "The Virtual University: A State of the Art." She discusses the issues that will need to be addressed if online education is to live up to expectations. Neville Holmes covers a related subject in his chapter "The Net, the Web, and the Children." He argues that the Web is an evolutionary, rather than revolutionary, development and highlights the division between the rich and the poor within and across nations. Continuing the WWW theme, George Mihaila, Louqa Raschid, and Maria-Esther Vidal look at the problems of using the Web and finding the information you want. Naren Ramakrishnan and Anath Grama discuss another aspect of finding relevant information in large databases in their contribution. They discuss the algorithms, techniques, and methodologies for effective application of scientific data mining. Returning to the Web theme, Ross Anderson, Frank Stajano, and Jong-Hyeon Lee address the issue of security policies. Their survey of the most significant security policy models in the literature shows how security may mean different things in different contexts. John Savage, Alan Selman, and Carl Smith take a step back from the applications and address how theoretical computer science has had an impact on practical computing concepts. Finally, Yuan Taur takes a step even further back and discusses the development of the computer chip. Thus, Volume 55 takes us from the very fundamentals of computer science-the chip-right to the applications and user interface with the Web.
Язык: Рубрика: Computer science /Статус предметного указателя: Готов указатель с номерами страниц ed2k: ed2k stats Год издания: 2001Количество страниц: 301Добавлена в каталог: 24.08.2015Операции: Положить на полку |
Скопировать ссылку для форума | Скопировать ID
Предметный указатель
Abbatel, J. 57 83 Abbott, C. 125 163 Ableson, H. 155 168 Access Control List (ACL) 219—220 Active reading 16 Active writing 15 Adali, S. 113 117 Adam, N. 153 168 ADEPT-50 197 Adhikary, J. 124 162 Adiwijaya, I. 153 168 Adjunct mode use of networks 25 Aggregation 205—206 Agrawal, R. 121 138 162 Aircraft design 158—159 Akamai 175 Akman, E. 151 168 Algorithms, design and analysis 181—182 Algorithms, new theories 182 Alta Vista 72 Ames, S.R. 197 234 235 Amir, A. 183 Amoroso, E. 201 209 210 231 Analyst Alice 212 Anderson, D. 127 163 Anderson, J. 190 231 Anderson, M. 202 231 Anderson, R.J. 186 190 192 205 206 213 214 217 228 231 234 Anderson, S. 6 46 Angelucci, R. 273 279 Anghel, M. 124 162 Anytime analysis 161 ANZLIC 90 Application incompatibility 206 Archie, J. 134 165 Arecibo radio telescope 127 Astronomy 179 Astrophysics, data mining 126—127 Asynchronous Transfer Mode (ATM) networks 175 Atalla, M.M. 238 278 Atluri, V. 153 168 Atmospheric Global Circulation Model (AGCM) 123 Austell, V.A. 209 233 Automated compliance verification 227—228 Avnur, R. 139 166 Axiom 178 B2B (business-to-business) 68 B2C (business-to-consumer) 68 Bacon 136 Bacsich, P. 11 47 Baden, S. 151 168 Badger, L. 198 231 Bailey-Kellogg, C. 141 154 166 168 Bajaj, C. 147 167 Baker, C. 151 152 168 Bakoglu, H.B. 276 278 279 Balabanian, N. 76 85 Balasubramanian, J. 151 168 Banday, A. 127 163 Bane, P.W. 54 82 Barbara, D. 122 135 162 Barksdale, G. 199 231 Barlow, J.P. 77 85 Barnes, J. 145 167 Baru, C. 151 167 Bassous, E. 242 247 273 278 Beazley, D. 152 153 168 Bell, D.E. 189 193 231 Bell-LaPadula (BLD) security policy model 189—199 Benkart, T. 231 Bennett, B. 6 46 Bennett, C. 127 163 Berdichevsky, D. 78 85 Berger, J.L. 198 233 Berghel, H. 68 72 83 84 Berlin, A. 130 164 Berners-Lee, T. 89 113 116 Berry, M. 122 125 162 163 Bersanelli, B. 127 163 Berson, T. 199 231 Bezdek, J. 135 165 Biba integrity model 189 207—209 222 Biba, K. 189 207 232 BiCMOS 240 Bioinformatics, data mining 131—132 Bishop, C. 136 137 165 Biswas, G. 125 163 Bitzer, D. 231 Blacker encryption devices 200—201 Blank, D. 72 84 Blaze, M. 227 232 Blocking features 123 Blom, R. 124 162 BLP 199 203 206—208 210 211 219 Blum, A. 136 165 Blum, M. 183 BMA security policy 190 212—214 Board, J. 145 167 Boebert, W.E. 227 232 Boehringer, K. 130 164 Bohrer, B., et al. 113 117 Boisvert, R. 151 168 Bolt, D.B. 73 84 Books 60—64 Books, content 62 Books, manufacture 61 Books, storage 62—63 Boolean matrix 222 BOOMERANG 127 Boothby, N.G. 75 84 Bosak, J. 70 84 Bosch, D. 124 162 Bouton, C. 6 46 Bowman, C. 114 118 Boyan, J. 157 168 Bradley, S.P. 54 82 Bradshaw, F.T. 197 234 235 Bradshaw, G. 135 136 165 Bradsher, M. 6 46 Bramley, B. 151 168 Bramley, R. 151 167 Branstad, M. 201 232 Bratko, I. 137 166 Bray, T. 70 84 Breg, F. 151 168 Brewer, D.F.C. 190 211 232 Brewington, B.E. 69 84 Bright, L. 113 117 British National Lottery 228—229 Brodley, C. 125 163 Brodley, C.E. 71 84 Brokers 115 Bruffee, K.A. 28 29 31 47 Bryan, G. 125 163 Brynjolfsson, E. 68 84 Bucchignano, J. 255 278 Buchanan, B. 159 168 169 Buchanan, D.A. 256 271 278 buckets 105—112 116 Buneman, P. 153 168 Burns, J.R. 239 278 Busnel, R.G. 54 82 Cambridge CAP machine 220 Candan, K.S. 113 117 Cant, C. 204 232 Cantwell, B. 133 165 capability 220—221 Carroll, B. 54 83 Caruthers, J. 129 164 Catlin, A. 151 153 168 Cattell, R.G.G. 100 117 CCITT X.509 recommendation 223 CD-ROM 64 Centroids 115 certificates 223 Certification practice statement 225—226 CGI-based web applications 17 Chakrabarti, S. 57 83 Chan, K. 129 164 Chanat, J. 124 162 Chandy, K. 151 167 Chapman, G. 133 165 Char, B. 151 167 Cheeseman, P. 140 166 Chemical engineering, data mining 127—130 Chen, H-C. 64 69 83 Chen, W. 278 Children 50 64—75 Children and Internet 65—66 Children and World Wide Web 69—70 Children, digital divide 73—75 Children, future 73—75 Children, infancy divide 75 Chinese Wall model 190 211—212 222 Chou, A. 139 166 CLARANS 124 Clark — Wilson model 190 209—211 221 Clark, D.D. 65 83 209 232 Classe, A. 54 82 Clustering 124 134—135 140—141 CMC 11 CMOS devices, 25-nm, design 266—273 CMOS devices, 25-nm, Monte Carlo simulations 272—273 CMOS devices, band-to-band tunneling current density versus electric field 270 CMOS devices, below 0.25 251—266 CMOS devices, channel profile design 260—262 CMOS devices, dopant number fluctuations 264—266 CMOS devices, gate electrode 258—260 CMOS devices, gate oxide 256—258 CMOS devices, global wires 276—278 CMOS devices, halo doping 262 CMOS devices, interconnect issues 273—278 CMOS devices, interconnect resistance 275 CMOS devices, interconnect scaling 273—275 CMOS devices, inversion layer quantization effect 258 CMOS devices, low-temperature 255 CMOS devices, polysilicon-gate depletion effects 271—272 CMOS devices, power supply 251—255 CMOS devices, power vs performance tradeoff 254—255 CMOS devices, relative performance 254 CMOS devices, retrograde doping 260—261 CMOS devices, short-channel device design 266—268 CMOS devices, source-drain doping requirements 263—264 268—270 CMOS devices, standby power 252 CMOS devices, threshold voltage 251—255 CMOS Inverter 239 273 CMOS technology 239 240 CMOS VLSI 238—242 COBE 127 Codewords 192 Coiera, E. 155 168 Collaborative discourse 15 Collaborative learning 6—16 24—25 30 Collaborative learning, online courses 8 Combined recency 112 Comerford, R. 51 82 Comiskey, J. 125 163 Commerce and industry and Internet 68 Commerce and industry and World Wide Web 71—72 Commercial-off-the-shelf (COTS) components 202 Common Criteria 189 200 Communication networks 175 Communication technology 50 Compartment 192 Compartmented Mode Workstation (CMW) 198 201—202 Completeness 96—97 102 Composability 199 204 Computational biology 178 Computational complexity 180—181 Computational geometry 175 Computational steering 152 computer networking 1—2 Computer simulation (QoSim) 43 Computer system, protection of 187—188 Computer-aided materials design (CAMD) 129 Condon, A. 173 183 Conferencing systems 7 Configuration Management 189 CONQUEST 124 Constant-field scaling 242—245 Constant-field scaling, effect on circuit parameters 244—245 Constant-field scaling, rules 242—244 Constant-voltage scaling 245—246 Constrained Data Item (CDI) 210 222 Coordinating Communicating Systems (CCS) 176 CORBA 113 Corbalis, M.C. 51 82 Corporate email 226—227 Cosmic background radiation (CMB) 126—127 Cosmology, data mining 126—127 covert channels 205 Craven, M. 139 166 Crawford, A.K. 73 84 Crippen, R. 124 162 Cryptography 175 Cunningham, D.J. 6 46 Curry, J. 32 47 Curtis, B. 228 232 Cybenko, G. 69 84 136 165 Dalton's equations 136 Damage criteria 191—192 Damocles 273 Damon, W. 78 85 Dancing in Cyberspace 27 DASL (DAV Searching and Locating) 114 Data diode 200 Data is scarce 156—159 Data management 152—153 Data Mining 119—169 Data mining, applications 122—134 Data mining, applications, astrophysics and cosmology 126—127 Data mining, applications, bioinformatics 131—132 Data mining, applications, chemical and materials engineering 127—130 Data mining, applications, flows 133—134 Data mining, applications, geological and geophysical 123—126 Data mining, approximation 122 143—151 Data mining, best practices 139—143 147—151 153—155 Data mining, compression 121 Data mining, compression, continuous attribute sets 147—149 Data mining, compression, data defined over geometry and topologies 144 Data mining, compression, particle position data 148 Data mining, constructive induction 138—139 Data mining, controlling the complexity of induction 141—142 Data modelling 152—155 Data reduction techniques 122 Data representation 153—155 Data sources, discovering 100—101 Data sources, selecting and ranking 101—104 data storage 64 Database management system (DBMS) 153 Dataquest 11 Davari, B. 273 279 Davison, S. 153 168 de Bernardis, P. 127 163 de Boor's function 157—158 de Swaan, A. 76 84 85 Dean, C. 124 162 Delayed communication 50 Delphi effect 44 Demmel, J. 151 168
Реклама
 |
|
О проекте
|
|
О проекте



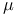 m
m